When running a business, your email is probably the most important tool you can utilize for customer service, sales and customer relations. But alongside that tool comes some underlying risk. Getting in front of hackers and malware emails is a lot easier than you think – the best part is that you can start protecting yourself at work and at home right now at no cost. That’s right, NO COST! Below are 10 examples of what you can do right now to make your business run smoother without the overshadowing thought that your email is being hacked.

- One of the most difficult parts of dealing with email hackers is how crafty they are which can be both a positive and negative. What do I mean by that? If you get an email from your Great Aunt Sally whom you haven’t heard from in a couple decades, requesting money urgently, it probably isn’t your Great Aunt Sally. On the other hand, they can also send you emails that seem totally legitimate, sometimes going as far as impersonating hospitals to get your private information to either track you or your clients. In either case, it is essential to take time to read the subject line and decide if it’s real or not which. Doing so does take valuable time from your work schedule. But now there is a solution that is free and you can download now. It’s called Ugly Email. What Ugly Email does is filter every email that comes through your inbox and marks them with an “evil eye” to indicate that email is nefarious. All you have to do is search for “Ugly Email” in Google Chrome Webstore to save yourself from tracked emails. It is a simple solution with great protection.
- Personal Security. You know all the questions Google asks you to confirm who you are? These questions aren’t used to annoy you. They are used to keep your account safe from those wishing to steal your information. Recovery email, phone number, two step verification and a difficult password go a lot further than you think. Google will send you alerts if someone tries to get into your account so if it isn’t you, you can deny access and report a problem, prompting Google to take steps to deal with the access breach.
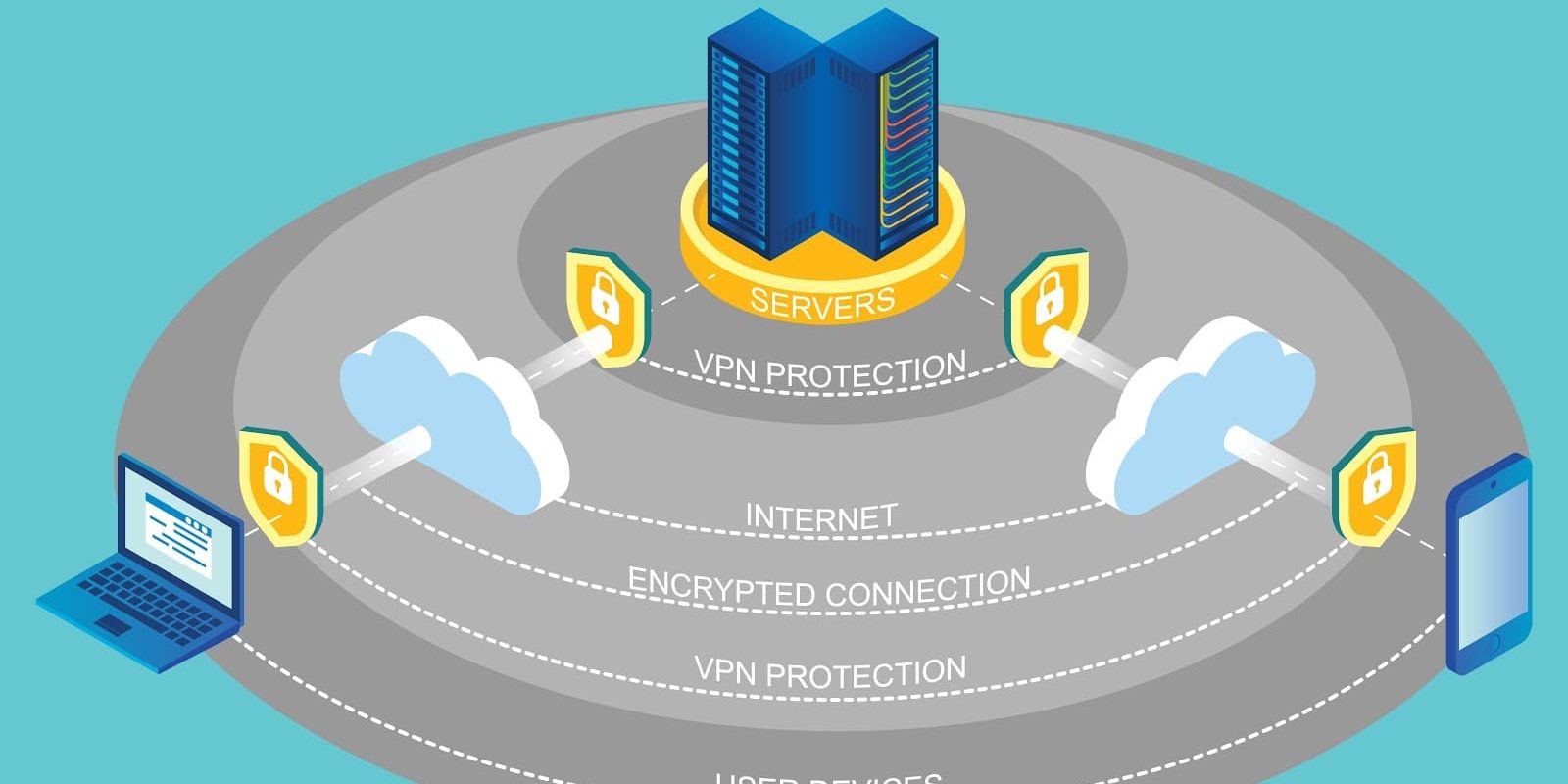
- Lastly is a VPN. We cannot stress enough how useful and important it is to download a VPN. This will allow you to create your own private network. Let’s say you have salespeople in the field and they need to request information or send information to your server. The VPN allows for that connection to be completely private so your information is virtually untouchable. The best part is that it is easy to download and use!
After you have taken the precautions above, it is essential to hire a professional who can work individually with your team and customize a cyber security plan for your business. Here at KMF Technologies we pride ourselves on 15 years of service across multiple sectors, from the healthcare industry to construction companies. We stay up to date on all things pertaining to cyber security and IT consultations. For more information on what KMF Technologies can do for you, contact us today!